- +41 58 307 05 55 (Europe)
- +1 305 728 53 69 (America)
- info@bestvision.group
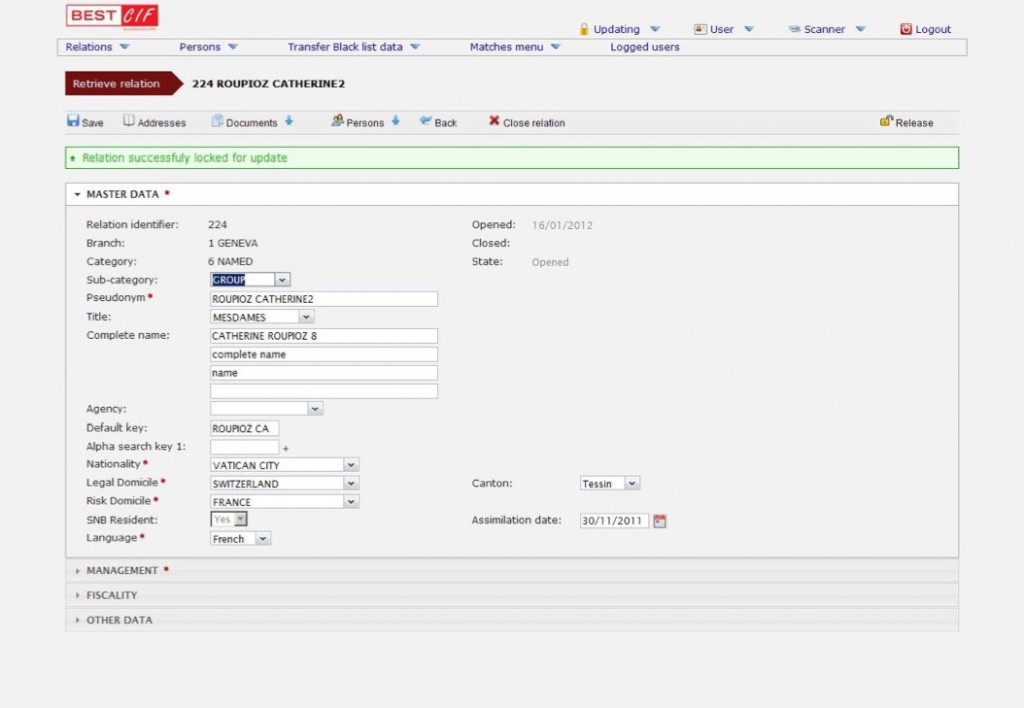
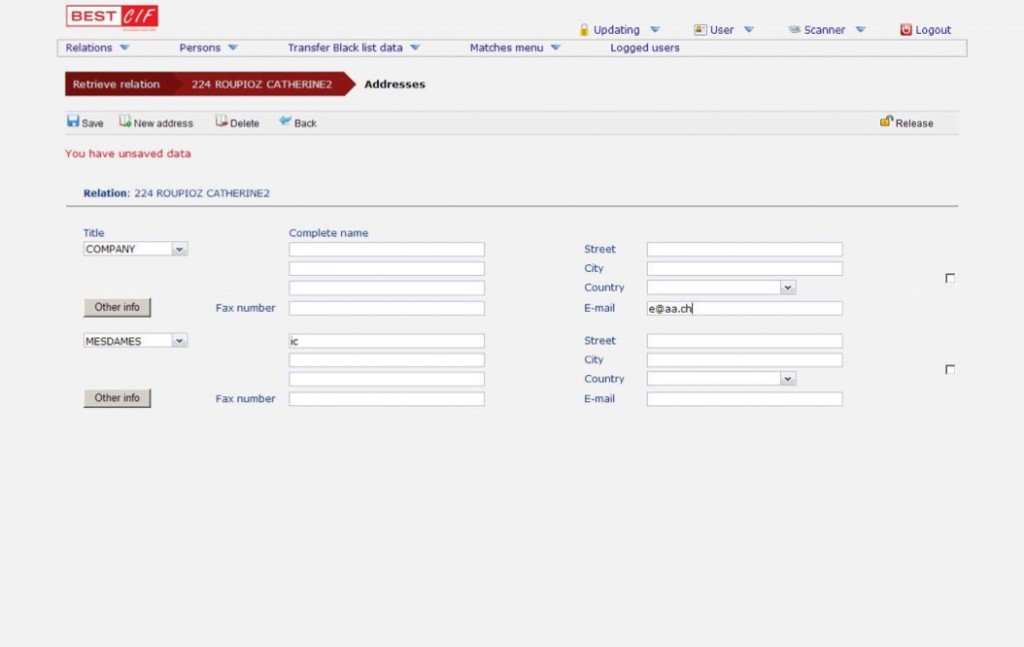
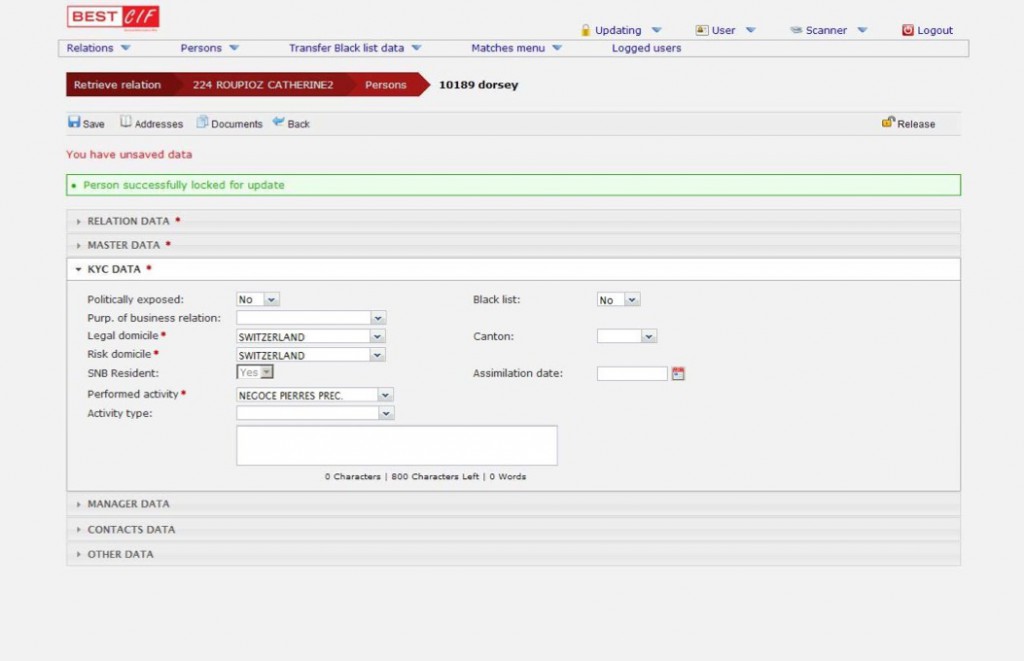
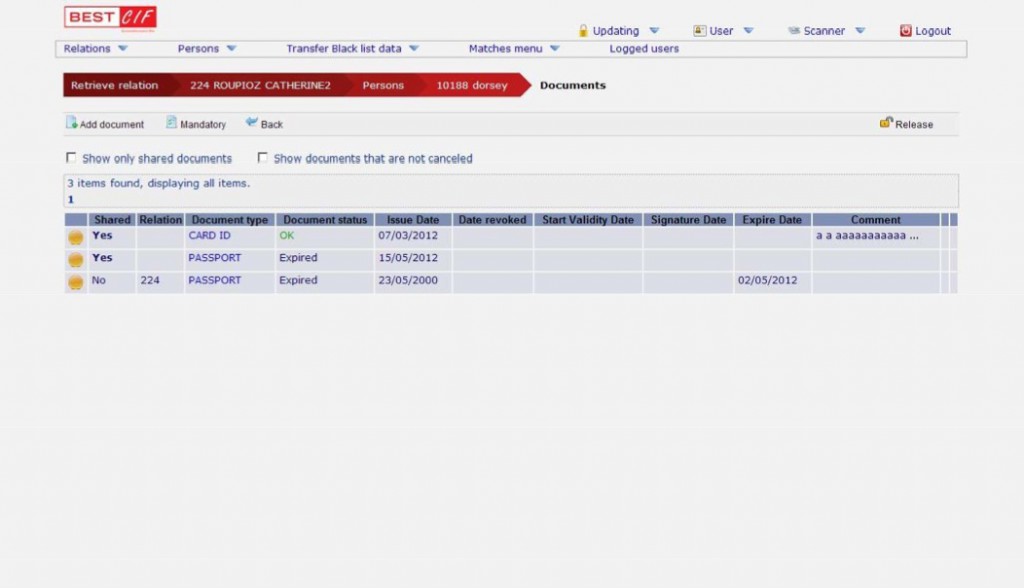
CENTRAL INFORMATION FILE
BEST CIF substitutes and improves the added physical security logics applied to the paper archives or to the stand alone workstation (usually placed in secured rooms) with an excellent improvement of the logical security level applied to clients confidential data.
Platform independent solution & available interface for various core banking systems.
Document Confidentiality System, in short:
- Central register front-end application to track any person entering the bank according to GAFI regulations.
- Client account full opening workflow management.
- Client Basic Data Management.
- Signed Documents/Mandates automatic production and management.
- Signed Documents/Mandates scanning and archiving Encrypted Data Management.
- High-level encryption system to manage client confidential data and documents.
- Strong authentication based on special smart cards.
SPECIFICATIONS
Requirements
Objectives
Advantages
Requirements
- Management of confidential information contained in the Central Register File in a computerized way (instead of in paper format or on stand alone workstations), using a solid cryptography solution.
- Improve the overall security level of the current client confidential data management system.
- Allow a computerized check between client confidential information and World Check to automate the Anti Money Laundering and Compliance Controls.
Objectives
Confidentiality
Hiding confidential data to who has not the permission for access them
Data Integrity
- To prevent against who does not have the authority for data inputting, deletion, modification, …
- Authentication to verify the sender of every action onto confidential data.
- Authorization to control the accesses, even at single function/object level.
- Data protection in regard to internal information technology department to grant that the IT doesn’t have the clear access to ciphered data, even in
case of physical theft of the disks. - To diminish the clear data exposure.
- To only decipher the closely necessary data and for the minor possible time.
Security
To guarantee that all the information transit only through “sure” channels.
Advantages
Authentication
One more user authentication level by the use of smart cards (logon on card = PIN request).
A sophisticated data encryption logic onto the database.
The information encryption onto the communication channels (between the client workstation and the server) during communications.
With BEST CIF it’s possible to limit the number of the person that have the access to the confidential information, and it also possible to discriminate allowed data access and allowed application functionalities user by user.
The applied high-level data encryption does not make the application heavier for the hardware equipment in a perceivable way. For cipher/decipher data the waiting times are extremely shorts.
BEST CIF contemplates the use of Java Smart Cards (meaning the Java Virtual Machine is entirely contained in the Smart Card) characterized by:
- Smart Cart ID
- PIN Code
- PUK Code
- User ID
- Kind of Smart Card
- User private key
The Java Smart Cards are initially pre-configured for each institute to be sure that only internally configured smart card could be recognized by the application. Moreover, all instances inside the Smart Cards are registered.


